The instant an Arduino or Raspberry Pi connects to the web (with a public IP) it is out there for anyone – or anything – to detect.
In our connected devices class, my classmates and I all saw this vulnerability firsthand. After leaving our connected thermostats on for a week, we experienced our devices being scanned and sometimes attacked by machines from across the globe.
NYU graciously provided information on the activity seen on our IP addresses. As you can see, our devices were detected thousands of times. (to be updated with stats)
Results
My device stood strong – the records on our server show some solid data coming from the device. In summary the device was:
✅ regularly reporting data (~once per-hour)
✅ accurate temperature readings (within 5 degrees celsius)
✅ accurate target temperature readings
First, somewhat regular reporting (No. of submissions) across the 7 days of testing:
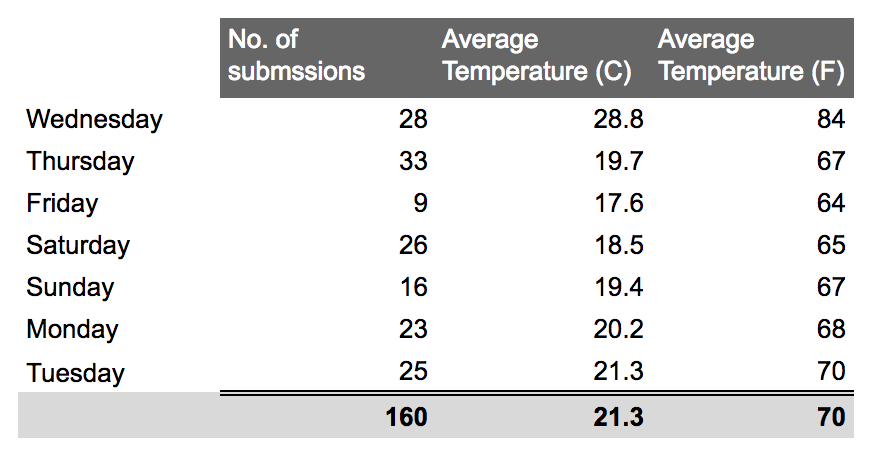
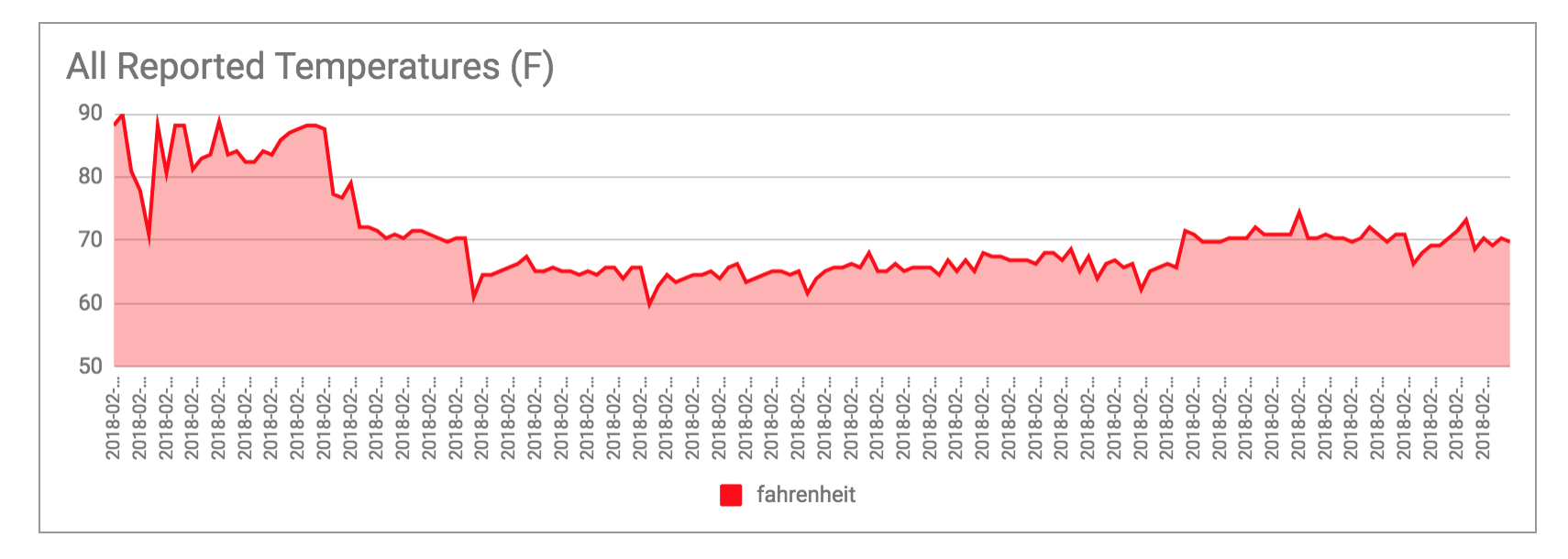
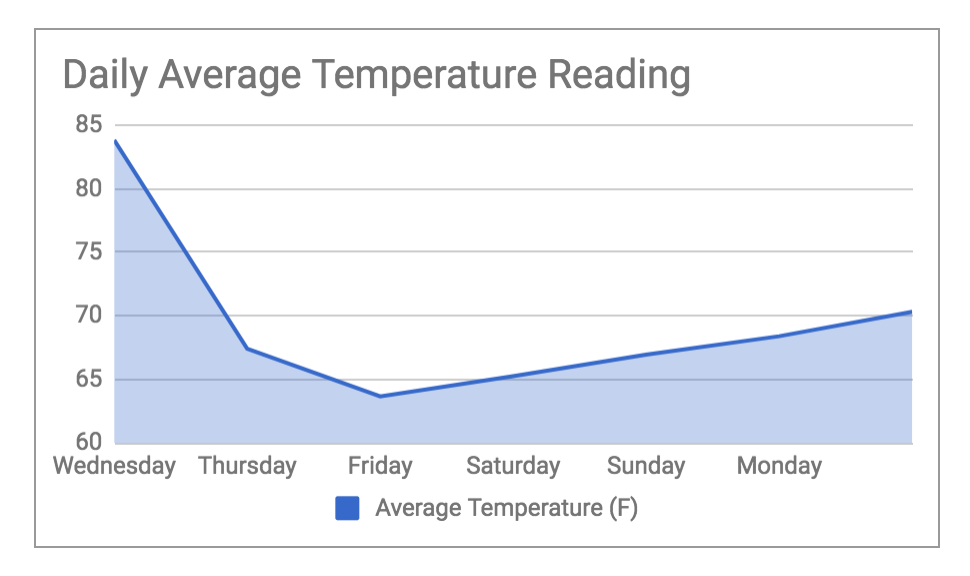
The temperatures started off a little wonky, then leveled out, Looking at every data point sent across the 7 days (above) – not bad! The daily averages (below) seem reasonable as well:
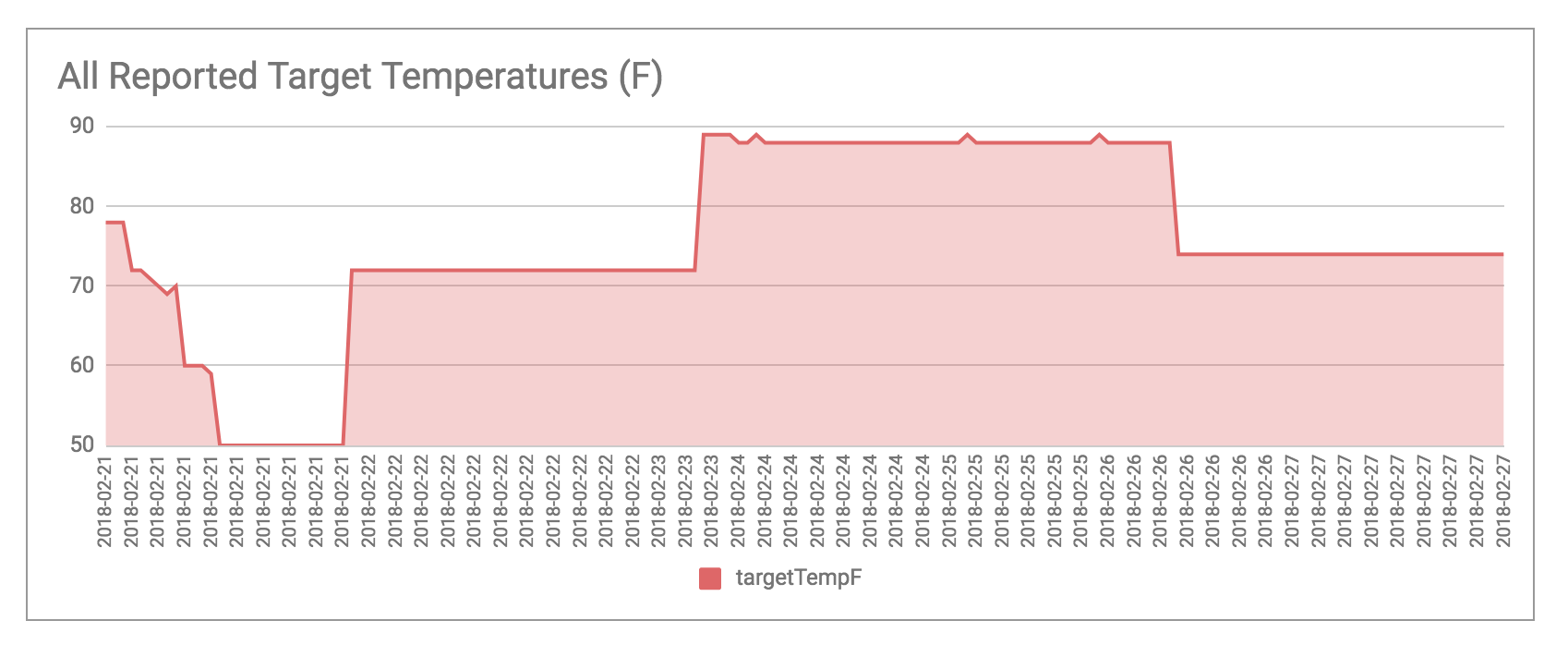
and the readings of the target temperature potentiometer (knob), which I manipulated a few times:
Analysis
Though arduinos and pis may seem like insignificant, itsy-witsy-wittle-baby computers, the level of control they are given over very real and tangible. With the proliferation of IoT devices in the home and workplace, the number of vulnerable baby computers grows!
What would you do if your apartment was getting too hot and your connected thermostat looked like this?

What would you do if your child’s toy or baby monitor was ‘hacked’?


One reply on “Cybersecurity Report: Connected DIY Devices”
[…] Consequentially, it was hanging out on the real, live internet and subject to attacks. Read more about the cybersec here. […]